Blog
Embracing OT-IT Convergence: How Automation Software Management Can Enhance OT Security
In the era of digital transformation, industries are increasingly embracing the convergence of Operational Technology (OT) and Information Technology (IT) systems. Industries are adopting software-defined architectures as they see a need for real-time data exchange, enhanced operational efficiency, and data-driven decision-making. OT-IT convergence enables seamless data flow between operational and enterprise systems, facilitating real-time monitoring, remote diagnostics, predictive maintenance, and process optimization.
To effectively secure these converged infrastructures while reaping the benefits of digital transformation, organizations are turning to well-architected automation software management environments aligned with established cybersecurity frameworks like the NIST Cybersecurity Framework. This emerging practice bolsters OT security through centralized software repositories, continuous vulnerability monitoring, role-based access control, and comprehensive audit trails and compliance reporting.
This blog will explore the driving forces behind OT-IT convergence, the rise of automation software management, and how these developments are reshaping industrial environments to unlock new business opportunities and competitive advantages.
The Rise of Automation Software Management and Impact on OT Security
As OT systems become more software-centric, the need for efficient and secure software management practices has become paramount. Automation software management has emerged as a critical function to support a DevOps-like environment for OT software management.
Automation software management encompasses the processes and tools used to manage the entire software lifecycle, from development and testing to initial commissioning, updates, and decommissioning. By adopting automation software management practices, organizations can streamline software deployment, updates, and lifecycle management across OT systems, improving operational efficiency and reducing the risk of human errors and security events.
There are four key approaches on how automation software management augments OT security:
1. Centralized Software Repository: A centralized software repository serves as a single source of truth for approved and validated software versions and source code to be deployed across OT systems. This mitigates the risk of incorrect software installations and ensures discoverability of unauthorized and unvetted software introduced into the OT environment. By maintaining a centralized repository, organizations can establish strict change control processes and enforce software integrity throughout the lifecycle. Additionally, this approach enhances traceability by maintaining a comprehensive software history, which is crucial for meeting industry and security framework requirements. This traceability is essential for incident response, compliance audits, and continuous improvement of security practices.
2. Continuous Vulnerability Monitoring: Automation software management tools can integrate with vulnerability scanning and threat intelligence services (i.e., OT monitoring tools like from Claroty, Nozomi, Dragos, etc.) enabling continuous monitoring and timely response to identified vulnerabilities. In the context of OT environments, where systems often run legacy software and have extended lifecycles, a comprehensive approach to vulnerability monitoring and management is crucial in reducing the attack surface and minimizing the risk of exploitation.
3. Role-Based Access Control (RBAC): Implementing RBAC within the automation software management environment ensures that only authorized personnel can deploy or update software components across OT systems. This access control mechanism primarily addresses security concerns by (i) reducing the risk of insider threats by limiting access to critical systems and (ii) preventing unauthorized changes that could potentially disrupt critical operations or introduce vulnerabilities.
4. Audit Trails and Compliance Reporting: Automation software management tools can provide detailed audit trails and compliance reports, enabling organizations to demonstrate adherence to regulatory requirements and industry standards. In highly regulated industries, such as energy, utilities, and manufacturing, maintaining comprehensive audit trails and demonstrating compliance with security standards is essential for ensuring operational resilience and minimizing legal and financial risks.
The NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) Cybersecurity Framework provides guidelines for organizations to better manage and reduce cybersecurity risk. With more sophisticated cyber threats occurring across many industries, organizations embraced the NIST Cybersecurity Framework as an essential foundation for managing cyber risk. This provides industry best practices for identifying, protecting against, detecting, responding to, and recovering from cyber intrusions. The guide on NIST Cybersecurity Framework (CSF): Aligning to the NIST CSF in the AWS Cloud enables customers to implement robust security controls, advanced monitoring, and resilient systems through the Amazon Web Services (AWS) cloud infrastructure. AWS’s security-focused approach allows organizations to accelerate their digital transformation confidently while assuring stakeholders of a strong cybersecurity posture, based on industry-leading practices. By aligning automation software management practices with the NIST framework, organizations can effectively address the unique challenges of securing converged OT/IT infrastructures.
The NIST CSF emphasizes the importance of identifying assets, assessing risks, implementing appropriate safeguards, and continuously monitoring and improving security posture. Automation software management tools can play a crucial role in supporting these activities by providing visibility, control, and automation capabilities across the software lifecycle.
Alignment of Automation Software Management on AWS With the NIST Framework
In the following section, we explore how automation software management on AWS aligns with each of NIST CSF’s core functions: Identify, Protect, Detect, Respond, and Recover. We will use Software Defined Automation’s (SDA) solution on AWS to highlight these aspects.
The AWS solution architecture for SDA’s solution is shown in Figure 1. The SDA solution on AWS is available as a Software-as-a-Service (SaaS) offering and has core features of Backup, Version Control, Brower-based Engineering, and Secure Remote Access with role-based access control. It leverages AWS services like Amazon S3 for secure storage and traceability of PLC source code versions, Amazon EC2 and NICE DCV for streaming vendor-specific IDEs over a web browser, and Amazon EC2 and Amazon DynamoDB for API driven capabilities for vendor IDE interaction. Users can access these applications through a web-based console, set project-level permissions, and enable temporary access to third-party collaboration. SDA enables secure connectivity between the cloud and the factory floor through a gateway server with an SDA agent, VPN client, and AWS IoT Core, facilitating PLC deployment from the cloud. It also provides a local client for code synchronization with the cloud repository. A REST API layer via Amazon API Gateway is also made available to allow custom application development and integrations. Data at rest and in transit between the gateway server and the AWS cloud are encrypted.
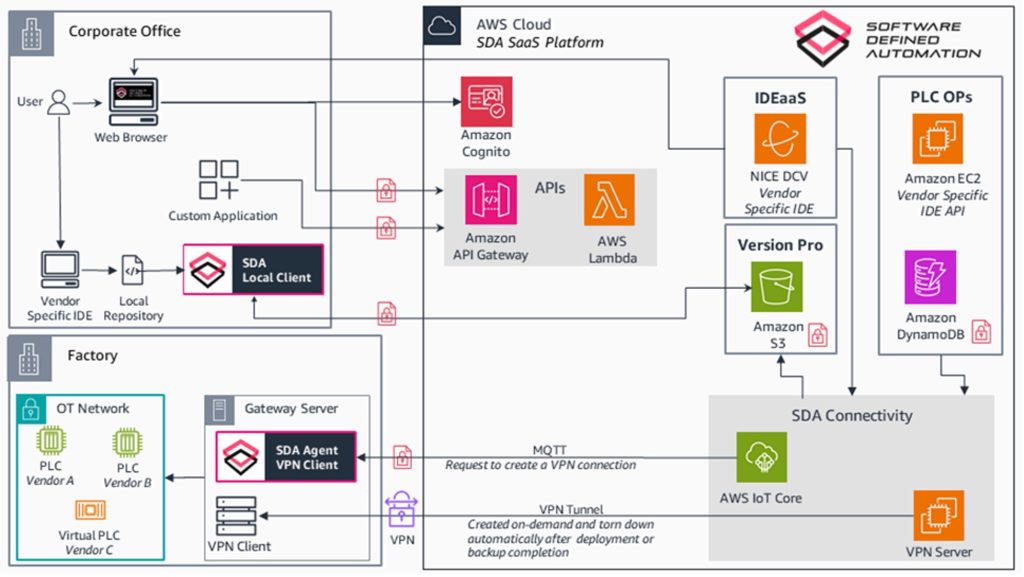
1. Identify:
This NIST function focuses on developing an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities. For OT systems on a manufacturing floor, this means identifying and understanding OT assets like programmable logic controllers (PLCs), supervisory control and data acquisition (SCADA) systems, and industrial control systems. It involves inventorying these systems, documenting dependencies and interconnections, and classifying data. This allows an organization to prioritize protection based on criticality and potential impact if compromised. Key activities in this function include network mapping, maintaining asset inventories, and conducting risk assessments of vulnerabilities. Manufacturers must identify and prioritize OT/IT systems, assess risks like unauthorized access or data theft, and understand regulatory issues. This enables them to focus cybersecurity activities and investments.
Automation software management solutions such as SDA’s PLC Version Control allows a user to catalog OT software assets (like PLC Programs) in a central location, including cataloging hardware configurations and software versions, providing a foundational understanding of the infrastructure’s digital landscape. Such detailed asset identification is essential for assessing and managing cybersecurity risks.
2. Protect:
The Protect function outlines safeguards to ensure delivery of critical services. For OT, this means installing security controls like access management, data security, maintenance, and protective technology. Examples include multi-factor authentication for OT system access, encryption to protect critical manufacturing data, using lock keys on PLCs, security-focused updates and patches for OT devices, and network segmentation to control access. The goal is developing layers of protection to secure OT systems from threats. Protection priorities depend on potential consequences if undermined and timeframes to restore manufacturing services. Manufacturers must restrict access to sensitive systems, implement security tools like firewalls and encryption, train employees on threats, perform regular system maintenance and upgrades, back up data, and more. Implementing safeguards reduces the impact of a potential cybersecurity event.
SDA’s Browser-based Engineering and Virtual PLC Management features reinforce the Protect function of the NIST CSF. This Integrated Development Environment as a Service (IDEaaS) reduces the risk of local software vulnerabilities by enabling secure remote access to PLCs from centrally managed PLC programming environments. SDA enables this connectivity to the on-premises factory network through a gateway server containing an SDA agent VPN client, which can establish a secure and short-lived VPN connection between the SDA applications in the cloud and factory floor on demand without the need to open any inbound ports. Additionally, all PLC access credentials are stored centrally, and users can get access rights to edit PLC code without directly accessing credentials. This methodology also enables secure collaboration with other vendors, ensuring they only get time-defined and secure access to the automation environment.
3. Detect:
The goal of the Detect function in the NIST CSF is to enable timely discovery of cybersecurity events. Examples of the function include defining events to monitor, establishing system telemetry, and continuous network/system monitoring. Manufacturers must monitor OT/IT environments to detect cyber incidents and anomalies that indicate vulnerabilities. Defining specific cyber events for security teams to look for ensures that monitoring efforts are targeted. Adequate sensor coverage and system telemetry is necessary for comprehensive awareness. Continuous monitoring enables rapid detection so manufacturers can respond before threats escalate into substantial disruptions.
SDA’s Backup and Version Control functionalities enhance the ability to detect changes in PLC code at any scheduled interval. The system’s code change visualization and alarm notification features enable quick identification of unauthorized alterations or anomalies in PLC code. Defined users can be informed upon any predefined type of change. Such advanced monitoring capabilities are crucial for the early detection of potential security incidents, aligning with the NIST framework’s emphasis on timely threat detection.
4. Respond:
The Respond function of the NIST CSF details appropriate activities to contain the impact of a cyber event. For manufacturers, this means executing response plans during actual cyberattacks against IT or OT environments. Manufacturers should have playbooks for prioritized responses, understand cyber incidents through forensics, mitigate vulnerabilities enabling attacks, eradicate threat actors from systems, recover capabilities and services disabled by attacks, and apply lessons learned. Swift and effective response limits damage from cyberattacks.
SDA can enable efficient incident response aligning to NIST’s Respond function. If a PLC code change is detected, users can be notified to analyze the changes that may pose a cybersecurity threat. Users can then use the platform’s version control and PLC management system that allows for swift rollback of changes, ensuring quick mitigation of cyberthreats. The malicious PLC code can be analyzed to understand the nature of the threat and the REST API can be used to scan the rest of the source for similar code. Single completely automated PLC deployments take minutes and can be parallelized to hundreds of PLCs through AWS’s scaling mechanisms – minimizing the Mean Time to Recover (MTTR). This immediate response capability is vital in reducing the impact of security incidents on critical infrastructure operations.
5. Recover:
The Recover function of the NIST CSF identifies proper activities to restore capabilities or services impaired by a cybersecurity event. For manufacturers, this focuses on restoring production capacity and business operations disrupted by cyberattacks against IT or industrial control systems. Key aspects include (i) recovery planning: developing and implementing processes and procedures to restore systems and assets affected by cybersecurity incidents, (ii) improvements: enhancing recovery strategies based on lessons learned from past incidents, and (iii) communications: coordinating restoration activities with internal and external stakeholders. Manufacturers should have continuity plans to enable manufacturing during outages, test restoration procedures regularly, apply lessons learned to boost resilience, keep leadership and stakeholders informed during recovery efforts, and integrate cyber resilience goals into the overall organizational culture. Robust recovery facilitates regained operational capacity after cyber incidents.
The Quick System Restoration feature of SDA is aligned with the Recover function of the NIST CSF and is supported by SDA’s Backup and Virtual PLC management features. These capabilities enable the rapid restoration of services and systems following a cybersecurity incident. Automated backups and virtualization facilitate quick recovery processes, ensuring minimal downtime and operational disruption.
Conclusion
As industries embrace OT-IT convergence and software-defined systems, the traditional air-gapped approach to OT security becomes increasingly inadequate. Automation software management emerges as a critical function that not only supports efficient software deployment and lifecycle management, but also introduces new opportunities to enhance OT security.
By leveraging well-architected automation software management environments and aligning with the widely-adopted NIST CSF, organizations can effectively secure their converged OT/IT infrastructures while reaping the benefits of digital transformation. Centralized software repositories, continuous vulnerability monitoring, role-based access control, and comprehensive audit trails and compliance reporting are just a few examples of how automation software management can strengthen the OT security posture of industrial environments.
This post originally appeared in the AWS for Industries blog. It is written by Software Defined Automation’s Josef Waltl and Leo Kilfoy and AWS’s Madhu Pai and Nishant Saini.
Stay up to date. Subscribe for our latest news.
