Secure Remote Access
Improve productivity and reduce downtime while improving factories’ security posture.
Secure Remote Access
Improve productivity and reduce downtime while improving factories’ security posture.
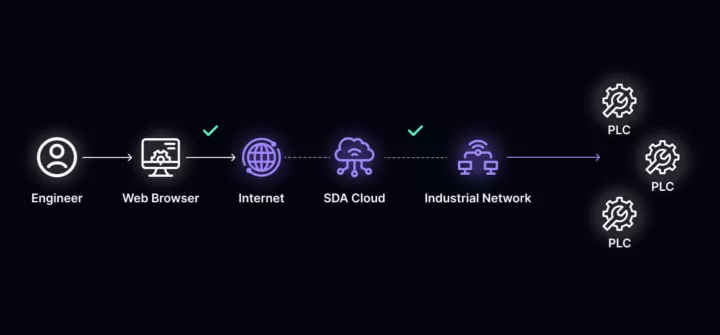
Security is paramount. The core intellectual property of many manufacturers is in the highly optimized control routines of their production equipment. This is why many factories are isolated from the rest of IT equipment. While this fortress approach can be effective, it’s far from efficient.
Local-only access means that every fix or routine change requires you to fly programmable logic controller (PLC) programmers around the world, which is expensive and creates long wait times. Alternatively, they can get on a video call with someone local to walk them through the process, but adding a non-expert intermediary introduces potential for error and accountability issues. The irony is that when security is burdensome, it leads to practices that create more vulnerabilities, such as putting code on USB drives or emailing it around.
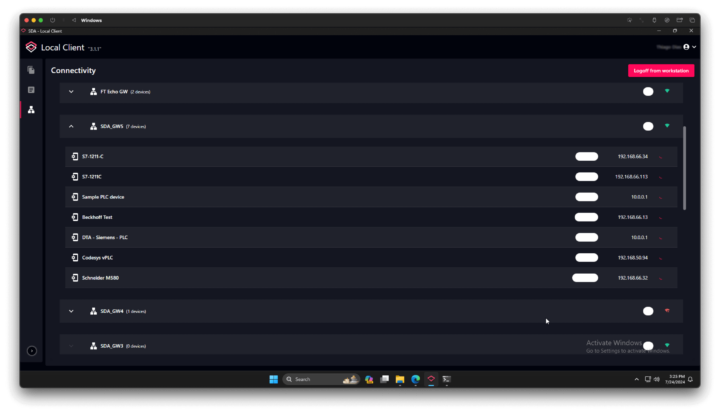
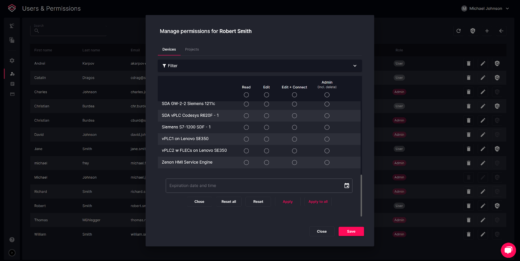
Software Defined Automation’s Secure Remote Access uses industry-leading, security-first practices, while letting you control who has access to which devices and when. This gives you the best of both worlds: allowing authorized personnel to perform necessary tasks remotely without compromising stringent security standards.